Thursday, December 29, 2016
Home »
COMPUTER MAINTENANCE & REPAIR.
» How to Manually Remove Computer Viruses Without Antivirus Software
How to Manually Remove Computer Viruses Without Antivirus Software
Do I Have a Virus? My Computer is Acting Weird!
If your computer is acting weird—displaying pop-ups from programs you've never heard of, showing your desktop icons running away from your computer mouse, or suddenly running terribly slow—your computer may be infected. These behaviors are more often than not a sign that a computer virus, worm, or other malicious software has managed to sneak past your firewall and anti-virus program.
You should definitely run a virus scan on your computer to see if the virus or worm can be detected; nevertheless, as my own experience shows, malicious software can hide from even a well-known anti-virus program. You may end up having to manually search for the invading software and remove it yourself, if you are trying to avoid a system restore, and this article will show you how to do that.
Neither malicious software nor anti-virus programs are created equal. In fact, this past August I was attacked by one of the most vicious Trojan horses created, fFollower.exe (well, the most vicious and evil Trojan I've come across).
All of a sudden I got a popup telling me to click to install "Windows Updates." Clicking the popup caused my computer to restart. Then a window opened saying something about "fFollower.exe," whatever that was, with a little picture of a devil. While I was pondering that, the window disappeared, and the next thing I knew, System windows, Internet Explorer windows, and JavaScript windows were popping up so fast my head was spinning. I almost thought I was in a scene from the Exorcist. The Trojan was creating more and more illegitimate processes, flooding the computer with useless tasks. I could predict the outcome ... a computer running slower and slower until the eventual and inevitable crash.
Time was running out for Ace (my computer has a name), and with every minute that passed, Ace was closer to death, I could just see it.
But what luck, I thought; I had just signed up with a new internet service provider, and received Norton AntiVirus Online from them. I started the Norton virus scan. I waited. Norton crawled along, and finally reported nothing but a tracking cookie. Evidently, my luck was out.
What could I do? Put Ace out of his misery? Or look online for a solution?
Computer viruses can quickly leave you with no other option then to shoot your computer.
Computer viruses can quickly leave you with no other option then to shoot your computer. | Source
So I searched the Web, and found software called Malwarebytes, which claimed to remove malware, spyware, adware, key loggers, and Trojans that most well-known anti-virus programs failed to detect. That was what I needed, I thought, so I downloaded a free version.
And Malwarebytes delivered: with just the "Quick Scan" option, it picked up a total of 40 computer viruses, worms, Trojans, spyware, and other malicious files that Norton Antivirus didn’t even have a clue about. Later I did a full system scan with Malwarebytes, and found 13 more viruses, including that evil Trojan fFollower.exe.
The full version of Malwarebytes, which I ended up buying, includes not only scheduled scanning and updating but real-time protection against hackers trying to break through your firewall. This real-time protection has prevented so many hacker attacks on my computer on a daily basis that I can’t even keep track of them.
Malwarebytes Is the Anti-Virus I Use
Malwarebytes Anti-Malware Premium LIFETIME Activation Key! (GENUINE & AUTHORIZED, Immediate Key Issued, No Waiting for CD) -- previously Professional [Download]
Malwarebytes Anti-Malware Premium LIFETIME Activation Key! (GENUINE & AUTHORIZED, Immediate Key Issued, No Waiting for CD) -- previously Professional [Download]
The full version of Malwarebytes, at about half the price of well-known anti-virus programs like Norton, provides real-time firewall protection, scheduled scanning, and scheduled updating.
Buy Now
Another Discovery: Threat Expert
While I was searching online regarding how to get rid of my computer virus, I also found Threat Expert, which anyone who owns a computer should know about, in case your virus protection software fails or is not available. This web site analyzes and reports the behavior of computer viruses, worms, Trojans, adware, spyware, and other security-related risks. These reports are useful for hunting the suckers down yourself, as they tell you the file names and aliases created, processes created, registry keys created, and other information about the virus.
Need to Manually Remove a Computer Virus Without Virus Protection Software?
I am a research junkie who loves to research anything and everything that crosses my path. However, on a computer, researching everything that crosses one's path is risky behavior, and I have suffered the consequences a few times. At times I have manually removed malware, like this Trojan horse, viruses, key loggers, and adware, because I did not have the money to keep my Norton Antivirus software updated as often as the manufacturers want us to.
Before We Start Our Malware Search-and-Destroy Project
Depending on the programming of the virus, spyware, adware, or other unwanted program, it may be possible to remove it yourself from an infected computer. However, it can be a long, tricky process, and can damage your files if some step does not work exactly as planned.
Therefore, I strongly recommend that before you go through the steps below, you do what you can to back up the information you have in your computer. If you don't have a complete back-up, follow the instructions below at your own risk.
Ideally you should always have a complete back-up of your computer. The back-up allows you to run a system restore, which will restore your computer to a previous state if all else fails. (And in addition a back-up will help you identify any new files that you did not install, which may be malicious.)
I also must advise you also that using good virus protection software, like Malwarebytes, to remove malware is faster and safer for your data.
Five Easy Steps to Remove Viruses and Other Malicious Software
1. Know Your Enemy
Any great war general will tell you to know your enemy, get inside their head, think like they do, act like they do, and become their best friend, as this will prepare you to overcome your enemy. So engage with the virus: keep an eye out for any security messages that pop up, as these usually provide the exact name of the virus that has infected your computer. If it gives you a security message that says "For More Info Click Here," or something else to click on, and it is not asking you to enter personal financial information or install anything, you may want to go ahead and click on it. Be prepared to write down any product name it gives you, or any file name and directory path (example: C:\Users\YourUserName\AppData\LocalLow\Temp\Virus). Remember, NEVER give out your personal financial information in these dialogues with malware.
Now if you were lucky enough to catch a security message and get the name of the virus itself, then you can continue on to Threat Expert and get all the information you can on that malicious software.
If you were only able to get a product name, then you need to do a search on it. Most likely, you’ll find out that the product is "fakeware" (malicious software that calls itself an anti-virus program).
In your search, it's a good idea to pursue results that link you to a forum, as you may find the information you need in discussions there, for example the name of the virus infecting your computer.
Once you have the name of the virus and the report from Threat Expert you can begin the hunt. It won't be a long hunt if you were able to get the directory from the "security" message, because that is where that little malicious bugger is hiding.
2. Block the Virus from the Startup List
You can’t kill the virus unless you put it to sleep first. So to put the virus to sleep we will end all the processes created by the virus.
A first step is to block the malicious program from starting itself up along with your usual programs every time your computer starts up. You can use System Configuration ("msconfig") to do this. One way to do this is to click the “Start” button on your desktop, type "System Configuration" into the "Search" field, and select “Start System Configuration” from the results. Or find it by clicking "Start," then "Control Panel," then "System and Security," and then "Administrative Tools," and then double-clicking "System Configuration."
System Configuration is great for helping with virus removal, allowing you to keep the virus turned off when you start up again. | Source
System Configuration opens the "General" tab, where you will need to select the circle next to "Selective Startup." Next, move to the “Startup” tab and go through the list there: select all the programs that have an unknown manufacturer and disable them, because programs with unknown manufacturers are almost always malware. Restart your computer to close any currently-running versions of the malware.
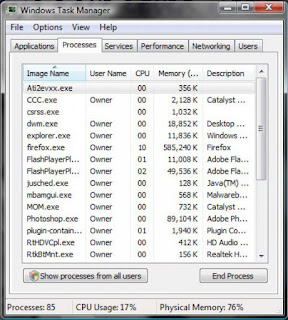
3. Start Task Manager and End Virus-Related Processes
When your computer restarts you will open your Task Manager immediately, which can be done quickest by pressing the "Ctrl," "Alt," and "Delete" keys all at the same time and then selecting "Start Task Manager" from the options that appear. Select the “Processes” tab and then compare the processes listed as running on your computer to the list of virus-created processes you got from the Threat Expert report or other research. Any processes running on your computer that match the ones on the report need to be ended, until all virus-created processes are gone.
4. Seek and Destroy That Malicious Software: Delete Its Files
Now we will go to the directory where the virus is and delete the virus. Tip: viruses like to hide themselves inside your “Temp” folder. If you got the directory path from the security message the virus gave you, then all you need to do is open up your computer's Explorer window and follow the path. For example, if you were looking for "C:\Users\YourUserName\AppData\LocalLow\Temp\Virus…" you would click on the "C" icon in Explorer, for the computer's hard drive, then click the “Users” folder, then click the “YourUserName” folder, and so on, until you get to the virus. Now delete any file names that match those on the virus report.
5. Seek and Destroy Some More: Remove Registry Keys
Finally, we will go into the Registry and remove the registry keys the virus put in. To go into the Registry, click the “Start” button on your desktop, click “Run,” type "regedit," and click "OK." Or type "regedit" in the search bar on your Start Menu, and select the Regedit program from your search results. You can find the exact name and directory path of the registry keys created by the virus from the Threat Expert virus report. Delete the registry keys that the virus created--do be careful to delete the exact keys you have in mind, no others--and you should be virus-free.
Congratulations! Now Change Your Passwords
Now that the malware is removed from your computer you need to change your passwords. You do not know what private information of yours the malware may have scraped from your keystrokes, or from the wonderful little cookies you gather from all the web sites you visit, and you don't know to whom the malware may have sold this information. So please remember to change all of your passwords once the virus has been removed.
















McAfee Antivirus is so important specially for the system on which protect your device from internet threats or save important data to kept safe.You can easily touch with the antivirus technicians by dialing Mcafee Tech Support Number and make your device secure from the threats.
ReplyDelete