Friday, December 30, 2016
7 Types of Computer Hardware You Should Understand
Your computing experience is made up of interactions with hardware and software. The hardware is all the tangible computer equipment, such as the monitor, central processing unit, keyboard, and mouse. The main body of a computer is the system unit. The system unit’s case houses a number of essential components.
453374.medium.jpg
1.The central processing unit (CPU) is responsible for processing most of the computer’s data, turning input into output.
As you might imagine, the speed and performance of the CPU is one of the biggest factors that determines how well a computer works. A CPU is a very small, thin silicon wafer that is encased in a ceramic chip and then mounted on a circuit board.
CPU speed is measured in gigahertz (GHz). The higher this measurement, the faster the CPU can operate. A hertz is a cycle per second; a gigahertz is 1 billion cycles per second. CPU speed is not the only measurement of its performance, though; different CPUs have efficiency-boosting technologies built into them that can increase data throughput in a number of ways.
A fairer comparison between two different CPUs is the number of instructions per second they can perform.
2.Memory consists of computer chips that hold data.
One type of memory, called Random Access Memory (RAM), forms the central pool of memory that a computer uses to operate. The more RAM a computer has, the more applications it can have open at once without the computer’s performance starting to bog down. More RAM can also make some applications perform better in general.
Memory capacity is measured in gigabytes (GB), which is a billion bytes. Most basic computers have at least 4GB today, with higher end systems having 16GB or more. Like the CPU, memory consists of small, thin silicon wafers, encased in ceramic chips and mounted on circuit boards. The circuit boards holding memory are called DIMMs, which stands for dual inline memory module.
3.A hard drive stores software.
When the computer is turned off, whatever is on the hard drive remains there, so you don’t have to reload software every time you turn on the computer. The operating system and your applications load from the hard drive into memory, where they run.
Hard-drive capacity is also measured in gigabytes (GB), like memory. A typical hard drive might be 500 GB or even 1 terabyte (1,000 GB) or more. Most hard drives sold today are the traditional mechanical type that use metal platters to store data with magnetic polarity, but a newer type, called a solid state hard drive (SSHD), uses a type of memory, resulting in a fast, quiet, and reliable (but expensive) storage alternative.
453376.medium.jpg
4.In addition to the components in the system unit, a computer may come with one or more input devices.
Input devices include keyboards, mice, trackballs, and touchpads.
5.Each computer has some type of display screen.
Depending on the type of computer, the display screen may be built-in, or may be a separate unit called a monitor with its own power cord, as shown. Some displays are touchscreen, so you can use your finger on the screen to provide input to the computer.
Display quality is measured in resolution — that is, the number of pixels (individual colored dots) that comprise the display at its highest resolution. A typical resolution for a notebook PC is 1920 x 1080, for example. The first number is the horizontal resolution and the second one is the vertical resolution.
The aspect ratio of a display is the ratio of its width to its height, expressed in pixels. Displays may either be standard aspect ratio (4:3) or widescreen (16:9). For example, a small device might have a maximum resolution of 800 x 600; if you simplify that to a fraction, it comes out to 4/3.
6.Most desktop and notebook computers come with an optical drive, which is a drive that will read CDs, DVDs, and/or Blu-ray discs.
Optical drives get their name from the way data is written and read on the disc. A laser light shines on the surface, and a sensor measures how much light is bounced back from a certain spot.
Some laptop computers come without DVD capabilities because you can download and install software or play videos and music from the cloud (that is, via the Internet), so it’s possible to get along just fine without the ability to play DVDs. However, most desktop computers still come with a DVD drive.
7.Whatever computer you have, you will probably want to use it to connect to the Internet. That means you will want it to have a network adapter in it.
That capability may be built into the computer, or it may be added to the computer via an expansion board or a device that plugs into a port.
Internet connectivity can be either wired or wireless. A wired connection requires you to connect a cable from the computer to the device that supplies your Internet connection (such as a cable modem). That type of cable and connection is known as Ethernet.
A wireless connection allows the computer to communicate with the Internet connection device through radio waves. The type of wireless connection used for Internet connectivity is called Wi-Fi, or wireless Ethernet.
If high-speed Internet service is not available in your area, you may need to use a dial-up modem to connect using your home telephone line. Dial-up modems are nobody’s first choice — they are old, slow technology and they tie up your phone line.
Steps in a Design Thinking Process
Steps in a Design Thinking Process
design_thinking_process.png
UNDERSTAND
Understanding is the first phase of the design thinking process. During this phase, students immerse themselves in learning. They talk to experts and conduct research. The goal is to develop background knowledge through these experiences. They use their developing understandings as a springboard as they begin to address design challenges.
OBSERVE
Students become keen people watchers in the observation phase of the design thinking process. They watch how people behave and interact and they observe physical spaces and places. They talk to people about what they are doing, ask questions and reflect on what they see. The understanding and observation phases of design thinking help students develop a sense of empathy.
DEFINE
In this phase of design thinking, students the focus is on becoming aware of peoples’ needs and developing insights. The phrase “How might we....” is often used to define a point of view, which is a statement of the:
user + need + insight
This statement ends with a suggestion about how to make changes that will have an impact on peoples’ experiences.
IDEATE
Ideating is a critical component of design thinking. Students are challenged to brainstorm a myriad of ideas and to suspend judgment. No idea is to far-fetched and no one’s ideas are rejected. Ideating is all about creativity and fun. In the ideation phase, quantity is encouraged. Students may be asked to generate a hundred ideas in a single session. They become silly, savvy, risk takers, wishful thinkers and dreamers of the impossible...and the possible.
PROTOTYPE
Prototyping is a rough and rapid portion of the design process. A prototype can be a sketch, model, or a cardboard box. It is a way to convey an idea quickly. Students learn that it is better to fail early and often as they create prototypes.
TEST
Testing is part of an iterative process that provides students with feedback. The purpose of testing is to learn what works and what doesn’t, and then iterate. This means going back to your prototype and modifying it based on feedback. Testing ensures that students learn what works and what doesn’t work for their users.
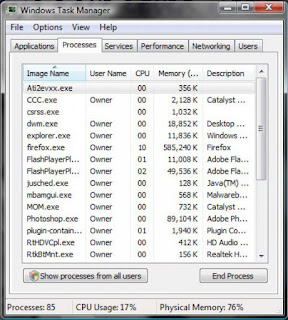
Hard Drive Repair Software to Solve Drive Data Loss Problems
How Hard Drive Data Get Lost?
When hard drive data is lost, the first thing that you must check is whether it is a physical hard drive problem to stop you from accessing the data, or just a logical problem to cause the data loss like deletion, format or hard drive partition loss, etc. In fact, the latter situation can be simply repaired by best hdd repair software. While to repair the former, you need to send your hard drive to the data recovery service.
Why can data lost from hard drive be recovered? Lost data was not really damaged, even if you have already emptied the Recycle Bin, used Shift Delete, or the hard disk has been standard/quick formatted, or partition is corrupted or lost. Only file system is changed in the disk. Like in a huge library, the books are still on the shelves, only the catalog which recorded the location of books is lost. And the library is the hard drive, the catalog is the file system of operating system, books are the clusters of hard disk.
check and repair disk error in Windows 10
Before trying a third-party hard drive repair software to recover data from a corrupted hard drive, we recommend you to try Windows built-in tool to check and repair disk error first. If it works, you can easily access your data. Here’s how to do it in Windows 10:
1. Open Computer, right-click the partition or drive that you want to check and click Properties.
2. Click Tools, under Error-checking, click Check now to see whether there exist any errors in your drive.
3. Select Automatically fix file system errors and Scan for and attempt recovery of back sectors.
4. Click Start.
Data Recovery Software to Repair Hard Drive Data Loss Problems
EaseUS Data Recovery Wizard Professional is a best hard drive data recovery software to perform hard drive recovery and solve all data loss problems including software crash, raw file system, formatted or damaged hard disk, virus attack, lost partitions, hard drive recovery and other unknown reasons under Windows. It recovers data from formatted partitions with original file names and storage paths.
Download
Win Version
Download
Mac Version
Step 1. Launch EaseUS Data Recovery Wizard and select the file types you want to recover. Then click "Next" button to move to the next step.
Select the files you want to recover from the hard drive
Step 2. Select the disk where you lost your data and click "Scan" button, the software will quickly scan the selected disk to find all your target files. If you lost your partition, select "Lost Disk Drives" and "Scan" to continue the recovery process.
Choose hard drive to be scanned
Step 3. After scan, you can preview all the listed recoverable files one by one and select out those you want. Then, click "Recover" button to get them back once. Here you should save all the recovered files on another disk to avoid data overwriting.
Preview and recover lost files and then you can repair hard drive
HOW TO INSTALL SECURITY CAMERA SYSTEM FOR A HOUSE
The idea of drilling holes through the walls of your house to run video and power cables for a security camera system might seem daunting; but many security systems come in all-included packages that make setting up your surveillance system a breeze. Read on for guidance on buying and installing your own home camera system.
1.Preparing Your Home
1.Make a diagram of your surveillance needs.
It is both expensive and impractical to monitor every square inch of your house, so you need to prioritize what areas you want to watch the most. Draw up a rough diagram of your house or print out the blueprints and note where you might want to place cameras. When you are done, check out each location to make sure it is not blocked by anything and provides the best view possible. You may want cameras for:
. Front and back doors.
.Off-Street Windows
.Large common spaces
.Driveways
.Porches
.Stairways[1]
2.Buy the right package to suit your needs. You can buy each piece individually, but it is generally cheaper and easier to buy bundled security systems. At minimum your system should have 1-3 cameras, a DVR (digital video recorder), appropriate wiring (siamese and BNC cables), and power cords. Unless you are choosing to monitor a large area, wireless cameras with wall mounting should cover your needs.
i.Basic Home Security: Get a package with 2-3 outdoor cameras (to monitor doors), and a DVR with at least 3 days of recording time.
ii.Monitoring Valuables/Young Children: 1-3 indoor wireless cameras can cover a small room effectively and stream the footage right to your computer.
3.Alternatively, buy your cameras individually. Once you know how many cameras you need, you'll need to think about what specific cameras you want. A home surveillance system can cost anywhere from a few hundred dollars to well over a thousand, so make sure you consider the type of cameras you need before buying -- the features below should be clearly labeled on the box. While you can buy all of the parts separately, buying a full "surveillance set" is usually cheaper and easier to install.
Wireless vs. Wired: Wireless cameras are easy to set-up without drilling or running cables through your house, but the quality can be sub-par the further they get away from the receiver. If you are covering a big area, go wired, but most houses find wireless and easier set-up process.
Indoor or Outdoor: Cameras that are not made to be place outside will quickly break when exposed to rain and humidity, so be sure to choose accordingly.
Motion Sensing: Some cameras will only record when they notice motion, saving space and energy while only capturing footage when someone is in the room.
Remote Viewing: Many high-end cameras offer the ability to stream their footage to your phone or laptop anywhere in the world, making it possible to check out your house through a provided program or app.
4.Set up a recording device and monitor. In order to store and view your footage you need a Digital Video Recorder (DVR). This device receives all of the video feeds and broadcasts them onto a monitor, usually a computer screen or small TV. DVRs have a variety of memory capacities that allow them to store a certain amount of video, from hundreds of hours to one day's worth of footage.
i.If you buy a complete surveillance set the DVR is usually included with the camera.
ii.Network Video Recorders (NVR) and analog recorders (VCRs), also available for purchase, work the same way as a DVR, using an internet signal (NVR) or blank tapes (VCR) to record instead of a digital hard-drive. The following installation tips will work here as well.
5.Test your equipment before installing. Make sure your cables, DVR, cameras, and monitor all work by connecting each one before you install anything.
2.Installing a Camera
1.Choose a high, broad angle for your camera. The best angle of any room is usually looking down from the corner where the ceiling meets the walls. Make sure you can clearly see all entries and exits and that the camera is near a power outlet.
If you are mounting a camera outside, place it above 10ft so that it cannot be easily knocked down.
2.Mount your camera to the wall. Some cameras come with sticky pads to adhere your camera to the wall, but screwing your camera in is the safest way to mount your cameras long-term. While every camera is different, most of them can be mounted the same way:
.Place the mount in it's desired location.
.Using a sharpie, make marks on the wall where each screw should go.
.Drill a hole for each screw using an electric drill
.Hammer in any molding pins.
.Screw the mount into the wall.
.Position the camera to your desired angle.
3.Attach your camera to a power source. Almost all cameras come with a power adaptor that plugs into a normal wall socket. Plug the small, round end into the power input on the back of the camera and plug the other end into the outlet.
i.If your power adaptor is missing or broken, contact your manufacturer.
4.Attach wired camera to your DVR. Surveillance equipment is connected using a BNC (Bayonet Neill–Concelman) connection. BNC cables are simple to use -- they are identical on both sides and you simply plug them into the appropriate port, turning a small nut on the end to lock it in place. Plug one end into your camera's "Output" and the other into one of the DVR "Input" ports.
.Note which input you plug into -- this is the input your DVR must be set to in order to view your camera's video.
.If your cable does not have a BNC connection you can buy a simple BNC adaptor online or at a hardware store. This will slip onto the end of your cable to make it BNC compatible.
5.Link wireless cameras to your computer. Wireless cameras will come with a software disc that you need to install to view your feeds. Follow the on-screen instructions to access your cameras.[7]
.Some cameras have a small receiver that attaches to your computer through a USB port. Make sure this is properly attached.
.Write down your camera's IP address (ex. 192.168.0.5) if provided -- this number can be typed into any web browser to view your camera remotely.
6.Attach the monitor to the DVR. This connection frequently uses a BNC cable as well, but some DVR's can attach with HDMI cables, or coaxial cables. Using your preferred connection, attach one end to the DVR's "Output" port and the other to the monitor's "Input."
.You can hook up as many cameras as your DVR has inputs -- it will automatically record every camera you install.
.Note which input you plug into-- this is the input you need to choose to see your cameras.
7.Troubleshoot any connection issues. Check that the camera, DVR, and monitor are all hooked up to a power supply and turned on. Make sure your cables are securely attached and that you have selected the right inputs for your DVR and monitor. Some monitors will display every camera at the same time, others have "input" buttons that allow you to switch between cameras.
3.Consolidating your Surveillance System
1.Create a central "surveillance hub." When you are wiring a lot of cameras at once, you'll need one simple place to bring all of the feeds together to your DVR. This should be a place that is easy to access, and where you can comfortably run wires from anywhere in the house. Attics, offices, and your internet router all make good places to base your surveillance system.
. You should only need one DVR for all of your cameras.
2.Use Siamese cables to wire your system effectively. The most common surveillance cable is a Siamese cable, named because it consists of two cables attached together. One is for power, and the other is for video. This means you will only have to run one wire through your house to set up each camera. The cable is usually sold as RG59 or RG6.[8]
. The braided red and black side is for power. Red is positive and black is negative.
.The singular, cylindrical cable is for video. Each end will have either a BNC attachment or a coaxial cable.
3.Use a power supply box to power multiple cameras through one outlet. Power boxes, available online and in hardware stores for $30-$50, allow you to power you cameras through a single wall outlet. They come with multiple ports, and are great for powering close-together cameras or cameras that aren't near an outlet, like attic cameras. However, you will need to run lengthy amounts of wire to attach each camera to the same box.
. Always attach the cameras before hooking the box to electricity.
.Make sure you buy a power supply box big enough to power each one of your cameras. They should list how many outlets they support on the box.
4.Attach each video cable to a separate DVR port. Your DVR can handle multiple cameras at once, allowing you to record every room in the house with only one box. Your monitor will then display every camera, or you will have to cycle through them using the "input" button on your DVR.
5.Hide your wires. To have a truly professional looking system you can run your cables through the walls and towards your surveillance hub. Be sure you know the layout of your walls and the location of any pipes, cables, or studs as you begin running wires. Running cables requires you to drill a hole in the wall, then thread the cable through the walls to your DVR through open spaces in your house, usually the attic.
.If you are not comfortable drilling into your walls and running cables through, call a professional carpenter or handyman to take care of the cabling.
.You can also secure cables to the walls or baseboards using a staple gun.
.Consider hiding cables under rugs, but tape them down so that no one accidentally trips.
6.Alternatively, call home-security specialists to set up a custom system. There are many home-security companies that will install cameras, motion sensors, and automatic emergency calling for you, though they cost much more than a typical DIY installation. However, if you have a large house, are uncomfortable with wiring, or want extra features like motion-sensors and alarm systems, call a security firm near you.
.ADT, LifeShield, Vivint, and SafeShield are larger, nationwide providers of home security systems.
How do I configure a wireless IP camera?
wikiHow Contributor
Plug the camera into your router using an ethernet cable. Run the software that came with your camera to set a password for the camera, and to see the IP address your router has assigned it. Type this IP address into your web browser address bar, and log in to your camera settings to get it running on your WiFi network. You can now unplug the camera and move it anywhere within range of the router signal.
Thursday, December 29, 2016
RAM of a Computer : Definition, Types and Form Factors
RAM of a Computer : Definition, Types and Form Factors
AM is an acronym for Random access memory. It is otherwise known as the primary memory of the computer and the hard drive is the secondary memory for bulk storage. The RAM of a computer is a memory that can be accessed randomly when the system is in use. It is a temporary memory for information storage because when there is power outage, the information goes and even when the computer is in use if not refreshed.
Going by the rule of thumb, the higher a computer memory, the greater its speed and vice versa. This knowledge is vital when purchasing a computer system and at least with a fair knowledge of the purpose the computer will serve. It is pertinent to state that computer motherboard has peculiar memory (RAM) it supports base on the motherboard Form factors. This will be discussed as we progress.
There are different types of computer RAM (Random Access Memory). The type of RAM a computer motherboard supports depend on the speed of the front side bus of its architecture. The front side bus of the motherboard architecture is the signal pathway between the computer processor and the memory. It houses the fastest chipsets (in terms of speed) of the motherboard circuitry and evidently the most important chipsets in the entire circuitry.
Types of RAM of a Computer
Broadly speaking there are two types of of a computer RAM( Random Access Memory). These are the Dynamic Random Access Memory (DRAM) and the Static Random Access Memory (SRAM). Anytime you here any discuss on the RAM of a Computer, it has to do with any of these two and their derivatives. Static RAM is not so popular because it is very expensive to develop and maintain. So this discourse will focus more on Dynamic RAM and its derivatives.
As indicated earlier the dynamic random access memory is use to describe the dynamic nature of the memory a situation when it retain its information only when refreshed constantly (called refresh signal), otherwise the information will go. Static RAM (SRAM) does not need constant refresh signal to retain information on it. However, because of its bulky nature and other limitations it did not gain popularity. Below are DRAM peculiarities and it derivatives.
FPM DRAM: FPM DRAM stands for Fast Page Mode Dynamic Random Access Memory. This came up with the early history of DRAM. It accesses a bit as a single task and finishes with it before accessing the next one. It operated at 176 MBPs.
EDO DRAM: EDO DRAM is an acronym for Extended Data-Out Dynamic Access Memory. EDO DRAM was an improvement on FPM DRAM as it does not need to wait for one single task to finish processing before accessing the next one. As soon as it commences the processing one bit, it starts accessing the next one immediately. This brought about greater speed and efficiency as compared with FPM DRAM. It operates at approximately 264MBPs.
SDRAM: SDRAM is an acronym for Synchronous Dynamic Random Access Memory. The initial DRAM uses asynchronous interface as it operates independent of the Processor. This was not good enough with respect to efficiency as computer usage kept growing in complexity and functions. It could not measure up with the demand placed on it by the processor. This challenge led to the emergence of SDRAM in the mid 1990s.
SDRAM synchronizes data between it and the processor concurrently thereby creating a continuous sequence of data processing with each carried out in turn. SDRAM runs at 133MHz, this was twice faster than EDO DRAM and three times faster than FTP DRAM. The major drawback of SDRAM was that it operates on Single Data Rate (SDR). This means it can only perform a single task per clock circle. This does not go well with contemporary demand in terms of computer speed. This led to the birth of Double Data Rate SDRAM (DDR SDRAM).
DDR SDRAM: As indicated from the foregoing, the Double Data Rate SDRAM was developed to solve the apparent shortcoming of Single Data Rate SDRAM. As the name implies, DDR SDRAM is able to move data at a speed faster than it immediate predecessor with a lesser energy consumption (2.5 volts) and up to 200400 MTPs. This was a great feat in the World of Computing. However as technology grows and higher Processor emerges, this became inadequate. The DDR SDRAM has 184 Pins and eight RAM chips with the ninth empty.
In the year 2003, a greater technology emerges that saw the birth of Double Data Rate type2 (DDR2 SDRAM). This again doubled the speed of first generation DDR SDRAM. DDR2 Dynamic RAM form factor operates at 4001066 MTPs (at 200533 MHz base) as per the rate of data transfer and even with a lesser power consumption (1.8 volts).
A further development emerged in the year 2007, still in this regard that bought about the birth of DDR3 SDRAM serving as the current market standard as at the time of this discourse. DDR3 further doubled the speed of DDR2 and with a lesser power consumption. DDR3 SDRAM rate of data transfer is 8002133 MTPs and 1.5 volts power consumption. DDR4 is expected to be on board soon. DDR3 technology utilizes both rising and falling edges of the clock circle a cardinal factor that underlies its speed. It has up to 8GB capacity.
RAM of Computer
RAM of Computer | Source
RAM of a Computer Form Factors
The form factors of random access memory described their kind of design, position of chips, their sizes, their compatibility with expansion slots and motherboards. Computer industry is driven by standards and the essence of this is to make available components that will be compatible with existing systems irrespective of the manufacturer. The RAM of a computer commonest form factors are as follows:
SIMM: This is one of the earliest RAM form factor. It is an acronym for Single Inline Memory Module (SIMM) that was used in the 1980s up to 1990s. The DIP Chips on the motherboard circuitry of the early computers occupies an unnecessary larger space more than what is obtainable today. It was then conceived that a small circuit board could be designed where such chips can be integrated for space economy and greater efficiency. More so, such boards can easily be removed.
SIMM has all the chips placed on one side of the Printed Circuit Board (PCB). Four SIMMs can be arranged in one row or space where the DIP chips hitherto occupies. The earliest set of Single Inline Memory Module has nine DIP chips integrated on the board and placed vertically very close to each other on their slots. This was a measure geared towards minimizing chips creep. Most SIMMs is 32-bit with 256kb to 1MB capacity.
If a Processor is 64-bit and SIMM is 32-bit, one most necessarily install more than one SIMM or change to Dual Inline Memory Module (DIMM) which will be discussed as we progress. This account for why more than one SIMMs is found on system boards. The first sets of SIMM came with nine DIP chips and with 30 pins (conductors) that interface via their slots with the motherboard circuitry. This was replaced with 72 Pins later in the 1990s.
DIMM: DIMM is an acronym for Dual Inline Memory Module. Unlike the SIMM, the DIMM form factor is 64-bit and has seen a remarkable growth since its birth. It came with RAM chips on both sides and 168 pins (conductors) during launch. DIMMS Slots is usually black while those of SIMM are white in colour. The shortcoming of SIMM form factor led to the birth of DIMM. Instead of installing more than one SIMM due to higher processor bytes, DIMM is preferred and performed better.
The conductors on DIMM are electrically isolated making separate contacts contrary to SIMM that are tied together. A number of modifications has occurred and still in the making. DDR3 DIMM is 240 Pins and it is electrically incompatibles with its predecessors. DIMM have a number of derivatives whose offshoot is dominant in computing industry.
RIMM: This is computer RAM form factor that came with the introduction of Intel 850 chipsets for Pentium 4 systems. It came with 184 pins (conductors) .This was in connection with Rambus DRAM (RDRAM) technology. RIMM is not an acronym like SIMM but a trademark term chosen by Rambus to describe the type of memory module. Rambus DRAM (RDRAM) is a superior memory as compared with its predecessors that creates multiple communication pathways between the memory and the system processor. This brought about greater speed and better memory efficiency.
The Printed Circuit Board containing the RAM chips has aluminum sheet that covers it called heat spreaders to protect the RAM from overheating. RIMM was very expensive and so it did not gain popularity. Alongside with this technology was development of Small Outline RIMM (SO-RIMM) for notebooks and similar computers that use smaller components.
SO-DIMM: Laptops and Notebooks that use smaller components with respect to size don’t use standard RAM form factors such as DIMM and SIMM. SO-DIMM is an acronym that stands for Small outline Dual Inline Memory Module. The SO-DIMM came with 72 and 144 Pins (conductors) with 32-bit and 64-bit respectively. With the passage of time, just as computer motherboards form factors keep changing in line with technology and users demand, the same is applicable to RAM of computer form factors. We have SO-DIMM that is 204 Pins in line with DDR type 3. So when making choices especially for the sake of upgrade these variations should be noted
Micro DIMM: This is one of the smallest RAM form factors used by mini and ultra light notebooks. It uses 64-bit memory module and the first set came with 164 Pins.
The foregoing reveals a phenomenal growth in computer Memory (RAM of a Computer) technology especially in the past two decades. Developers and manufacturers of computer components cannot rest on their oars at any level of achievement at any point in time. Because, growth and improvement in one aspect of the system technology, will invariably require others to follow suit.
How to Manually Remove Computer Viruses Without Antivirus Software
Do I Have a Virus? My Computer is Acting Weird!
If your computer is acting weird—displaying pop-ups from programs you've never heard of, showing your desktop icons running away from your computer mouse, or suddenly running terribly slow—your computer may be infected. These behaviors are more often than not a sign that a computer virus, worm, or other malicious software has managed to sneak past your firewall and anti-virus program.
You should definitely run a virus scan on your computer to see if the virus or worm can be detected; nevertheless, as my own experience shows, malicious software can hide from even a well-known anti-virus program. You may end up having to manually search for the invading software and remove it yourself, if you are trying to avoid a system restore, and this article will show you how to do that.
Neither malicious software nor anti-virus programs are created equal. In fact, this past August I was attacked by one of the most vicious Trojan horses created, fFollower.exe (well, the most vicious and evil Trojan I've come across).
All of a sudden I got a popup telling me to click to install "Windows Updates." Clicking the popup caused my computer to restart. Then a window opened saying something about "fFollower.exe," whatever that was, with a little picture of a devil. While I was pondering that, the window disappeared, and the next thing I knew, System windows, Internet Explorer windows, and JavaScript windows were popping up so fast my head was spinning. I almost thought I was in a scene from the Exorcist. The Trojan was creating more and more illegitimate processes, flooding the computer with useless tasks. I could predict the outcome ... a computer running slower and slower until the eventual and inevitable crash.
Time was running out for Ace (my computer has a name), and with every minute that passed, Ace was closer to death, I could just see it.
But what luck, I thought; I had just signed up with a new internet service provider, and received Norton AntiVirus Online from them. I started the Norton virus scan. I waited. Norton crawled along, and finally reported nothing but a tracking cookie. Evidently, my luck was out.
What could I do? Put Ace out of his misery? Or look online for a solution?
Computer viruses can quickly leave you with no other option then to shoot your computer.
Computer viruses can quickly leave you with no other option then to shoot your computer. | Source
So I searched the Web, and found software called Malwarebytes, which claimed to remove malware, spyware, adware, key loggers, and Trojans that most well-known anti-virus programs failed to detect. That was what I needed, I thought, so I downloaded a free version.
And Malwarebytes delivered: with just the "Quick Scan" option, it picked up a total of 40 computer viruses, worms, Trojans, spyware, and other malicious files that Norton Antivirus didn’t even have a clue about. Later I did a full system scan with Malwarebytes, and found 13 more viruses, including that evil Trojan fFollower.exe.
The full version of Malwarebytes, which I ended up buying, includes not only scheduled scanning and updating but real-time protection against hackers trying to break through your firewall. This real-time protection has prevented so many hacker attacks on my computer on a daily basis that I can’t even keep track of them.
Malwarebytes Is the Anti-Virus I Use
Malwarebytes Anti-Malware Premium LIFETIME Activation Key! (GENUINE & AUTHORIZED, Immediate Key Issued, No Waiting for CD) -- previously Professional [Download]
Malwarebytes Anti-Malware Premium LIFETIME Activation Key! (GENUINE & AUTHORIZED, Immediate Key Issued, No Waiting for CD) -- previously Professional [Download]
The full version of Malwarebytes, at about half the price of well-known anti-virus programs like Norton, provides real-time firewall protection, scheduled scanning, and scheduled updating.
Buy Now
Another Discovery: Threat Expert
While I was searching online regarding how to get rid of my computer virus, I also found Threat Expert, which anyone who owns a computer should know about, in case your virus protection software fails or is not available. This web site analyzes and reports the behavior of computer viruses, worms, Trojans, adware, spyware, and other security-related risks. These reports are useful for hunting the suckers down yourself, as they tell you the file names and aliases created, processes created, registry keys created, and other information about the virus.
Need to Manually Remove a Computer Virus Without Virus Protection Software?
I am a research junkie who loves to research anything and everything that crosses my path. However, on a computer, researching everything that crosses one's path is risky behavior, and I have suffered the consequences a few times. At times I have manually removed malware, like this Trojan horse, viruses, key loggers, and adware, because I did not have the money to keep my Norton Antivirus software updated as often as the manufacturers want us to.
Before We Start Our Malware Search-and-Destroy Project
Depending on the programming of the virus, spyware, adware, or other unwanted program, it may be possible to remove it yourself from an infected computer. However, it can be a long, tricky process, and can damage your files if some step does not work exactly as planned.
Therefore, I strongly recommend that before you go through the steps below, you do what you can to back up the information you have in your computer. If you don't have a complete back-up, follow the instructions below at your own risk.
Ideally you should always have a complete back-up of your computer. The back-up allows you to run a system restore, which will restore your computer to a previous state if all else fails. (And in addition a back-up will help you identify any new files that you did not install, which may be malicious.)
I also must advise you also that using good virus protection software, like Malwarebytes, to remove malware is faster and safer for your data.
Five Easy Steps to Remove Viruses and Other Malicious Software
1. Know Your Enemy
Any great war general will tell you to know your enemy, get inside their head, think like they do, act like they do, and become their best friend, as this will prepare you to overcome your enemy. So engage with the virus: keep an eye out for any security messages that pop up, as these usually provide the exact name of the virus that has infected your computer. If it gives you a security message that says "For More Info Click Here," or something else to click on, and it is not asking you to enter personal financial information or install anything, you may want to go ahead and click on it. Be prepared to write down any product name it gives you, or any file name and directory path (example: C:\Users\YourUserName\AppData\LocalLow\Temp\Virus). Remember, NEVER give out your personal financial information in these dialogues with malware.
Now if you were lucky enough to catch a security message and get the name of the virus itself, then you can continue on to Threat Expert and get all the information you can on that malicious software.
If you were only able to get a product name, then you need to do a search on it. Most likely, you’ll find out that the product is "fakeware" (malicious software that calls itself an anti-virus program).
In your search, it's a good idea to pursue results that link you to a forum, as you may find the information you need in discussions there, for example the name of the virus infecting your computer.
Once you have the name of the virus and the report from Threat Expert you can begin the hunt. It won't be a long hunt if you were able to get the directory from the "security" message, because that is where that little malicious bugger is hiding.
2. Block the Virus from the Startup List
You can’t kill the virus unless you put it to sleep first. So to put the virus to sleep we will end all the processes created by the virus.
A first step is to block the malicious program from starting itself up along with your usual programs every time your computer starts up. You can use System Configuration ("msconfig") to do this. One way to do this is to click the “Start” button on your desktop, type "System Configuration" into the "Search" field, and select “Start System Configuration” from the results. Or find it by clicking "Start," then "Control Panel," then "System and Security," and then "Administrative Tools," and then double-clicking "System Configuration."
System Configuration is great for helping with virus removal, allowing you to keep the virus turned off when you start up again. | Source
System Configuration opens the "General" tab, where you will need to select the circle next to "Selective Startup." Next, move to the “Startup” tab and go through the list there: select all the programs that have an unknown manufacturer and disable them, because programs with unknown manufacturers are almost always malware. Restart your computer to close any currently-running versions of the malware.
3. Start Task Manager and End Virus-Related Processes
When your computer restarts you will open your Task Manager immediately, which can be done quickest by pressing the "Ctrl," "Alt," and "Delete" keys all at the same time and then selecting "Start Task Manager" from the options that appear. Select the “Processes” tab and then compare the processes listed as running on your computer to the list of virus-created processes you got from the Threat Expert report or other research. Any processes running on your computer that match the ones on the report need to be ended, until all virus-created processes are gone.
4. Seek and Destroy That Malicious Software: Delete Its Files
Now we will go to the directory where the virus is and delete the virus. Tip: viruses like to hide themselves inside your “Temp” folder. If you got the directory path from the security message the virus gave you, then all you need to do is open up your computer's Explorer window and follow the path. For example, if you were looking for "C:\Users\YourUserName\AppData\LocalLow\Temp\Virus…" you would click on the "C" icon in Explorer, for the computer's hard drive, then click the “Users” folder, then click the “YourUserName” folder, and so on, until you get to the virus. Now delete any file names that match those on the virus report.
5. Seek and Destroy Some More: Remove Registry Keys
Finally, we will go into the Registry and remove the registry keys the virus put in. To go into the Registry, click the “Start” button on your desktop, click “Run,” type "regedit," and click "OK." Or type "regedit" in the search bar on your Start Menu, and select the Regedit program from your search results. You can find the exact name and directory path of the registry keys created by the virus from the Threat Expert virus report. Delete the registry keys that the virus created--do be careful to delete the exact keys you have in mind, no others--and you should be virus-free.
Congratulations! Now Change Your Passwords
Now that the malware is removed from your computer you need to change your passwords. You do not know what private information of yours the malware may have scraped from your keystrokes, or from the wonderful little cookies you gather from all the web sites you visit, and you don't know to whom the malware may have sold this information. So please remember to change all of your passwords once the virus has been removed.
5 Symptoms of a RAM Problem and How to Fix It
WHAT IS RAM?
Random Access Memory, or RAM, is a way for your computer to store temporary data, rather than in a cache or permanent storage. Storage, often wrongly referred to as memory, is permanent data stored on a hard drive or solid state drive. A CPU cache is a small amount of often-needed memory that is stored on a CPU chip. Both the RAM and CPU cache are temporary data stores that are cleared when your computer is turned off.
One way to think of the difference between these different types of storage is to imagine them as paper documents. The cache is a list of names or numbers you constantly refer to and keep close at hand. A folder full of papers you may need for your current task is similar to computer memory or RAM. The file cabinet full of folders for all your projects is like the storage on your hard drive.
Memory problems are less common than other computer problems because memory sticks have no moving parts and thus fewer points of failure. However, due to this many RAM problems go undiagnosed. Memory usually will last longer than other computer components so manufacturers offer longer warranties for it than other parts. If you buy brand name memory it will likely have a lifetime warranty.
Symptoms of a RAM Problem
When you first turn on your computer it runs fine, but as you go about your business you notice that its performance diminishes. By lunch time, websites take minutes to load and local programs run at a snail's pace. This type of gradual deterioration of PC performance, especially with memory-intensive programs, may be caused by a RAM problem.
Your computer randomly restarts while you are in the middle of something or freeze sporadically. It may also reboot almost immediately upon opening the desktop. This could be a sign of faulty RAM.
A blue screen with white text flashes before restarting. Blue-screen errors are annoying because you don't even have a chance to read the error message. Bad RAM is one thing that cause them.
Files—particularly ones you frequently access and save—seem to be inexplicably corrupted. RAM issues can lead to this problem, which can worsen over time. The file structure of your hard drive may slowly degenerate and you will no longer be able to boot your machine.
Your attempts to install a new program repeatedly fail for unknown reasons. You try to reinstall the operating system, but keep getting odd error messages.
There are certainly a variety of problems that could cause the issues above, but faulty RAM is an often-overlooked root cause of inexplicable issues. If you have one or a combination of the above problems you are likely facing a memory issue.
What Causes Memory Damage?
Power surges can damage most computer components, including RAM. You should plug your computer and other expensive electronics into a surge protector. Make sure you know the difference between a surge protector and a power strip.
Before you handle any parts in your computer, make sure you ground yourself by touching a piece of grounded metal to discharge static electricity. Electrostatic discharge can damage your computer.
Excessive heat can cause RAM and other parts to wear out over time. Individual components can overheat, or heat from one component can cause damage to adjacent parts.
If you have overclocked any part of your computer incorrectly, it may cause damage in the form of excess heat.
Your memory module may have some fault that passed through quality control and worsened over time. This is the most likely cause behind a damaged RAM.
It is also possible that the memory module is fine, but one or more memory slots on your motherboard are defective, hindering the RAM's performance. The defect may even be so bad that it damages the memory stick.
Upgrading and Repairing PCs (22nd Edition)
Upgrading and Repairing PCs (22nd Edition)
Buy Now
Diagnosing the Problem
If the symptoms started after you recently added more memory, the new module could be faulty. This seems obvious, but any time a problem begins after making a change, first check to see if the change caused the problem.
Your computer may produce multiple beeps or a continuous beep when you turn it on. These beeps can indicate many different problems, including being a symptom of bad RAM. Beep codes vary depending on the manufacturer of your BIOS. You can look up the beep codes for your specific computer to figure out its specific problem.
If you are not comfortable fixing your computer yourself, I recommend taking your computer to a local repair store rather than a big retail store. Big stores are in the business of selling additional parts, not fixing problems.
If you are an advanced user, there are diagnostic programs that can help you figure out if you have a memory problem. Your computer may have one pre-installed by the manufacturer or you can download a third-party program. The Windows Memory Diagnostic by Microsoft is also good if you suspect memory problems on a Windows PC.
If the above programs indicate your memory sticks are functioning, but you still suspect a RAM problem or if you need to find which memory module is the problem, you can try removing the modules and placing them in different slots.
Memory modules, pictured in the image above, are small circuit boards that lay perpendicular to the motherboard. Note that I removed many of the other components to make the memory more visible. If your computer has more than one module you should remove all of them except one and then run the diagnostic tests above or perform the task that normally causes the problem.
Fixing the Problem by Removing Memory
To remove a RAM module you need to press the tiny levers on each end to release it.
Test each of your memory modules one at a time to find which ones are bad. When you find the sticks that are bad you can order replacements. It is possible all the memory modules are damaged if your computer experienced a serious power surge.
If all the memory modules appear bad, then the problem is likely with the memory slot itself. Try testing each memory module in each of the memory slots to find if one of the slots is faulty. To fix a faulty slot you would need to replace your motherboard.
When replacing a module, make sure the indention on the bottom is lined up correctly with the slot and then press it in until you hear the levers snap. Note that some levers do not make a snapping sound.
RAM Slot Levers
The levers for the memory slot are white in this example.
The levers for the memory slot are white in this example.
Other Possible Problems
RAM problems often go undiagnosed, but they also can be misdiagnosed. Some common problems that have nothing to do with memory can cause the symptoms listed above:
Many of the symptoms listed above can actually be caused by a hard drive problem. You can run a utility called CHKDSK by pressing the Windows button and R at the same time, typing CHKDSK into the dialog box, and pressing enter. Alternatively, you can click on Computer, right-click the drive you intend to scan, click Properties, then the Tools tab, and click Check now. Note you will need to restart your computer. Also, be aware this process may take an extended amount of time to finish running. If you hear your hard drive making lots of noise during normal operation, it may be the cause of your problems. Defragmenting your drive every few months is a good idea as well.
If the performance problems occur during graphic-intensive programs such as games or rendering, your graphics driver could be outdated. Be sure to always keep your drivers up to date.
Excessive heat in your machine can cause a variety of problems.
Random reboots can be cause by a failing power supply.
Dirt and dust can also cause issues that look like memory problems. It is a good idea to clean dust out of your computer at least once a year, more often if you have furry pets.
Your computer can also have a virus. Note that many people automatically assume any problem with their computer is caused by a virus and many large retail repair stores frequently misdiagnose hardware problems as viruses. Make sure you have a good anti-virus program and run scans on a regular basis.
Wednesday, December 28, 2016
TYPES OF COMPUTER MOUSE DEVICES
TYPES OF COMPUTER MOUSE DEVICES
Let's talk about all of them and how they work.
WIRELESS MOUSE:
GSTICK MOUSE: Gordon Stewart designed the Stick to add a more authentic and natural feel to artistic manipulations on both Macs and PCs. ...
OPTICAL MOUSE: ...
A TRACKBALL MOUSE: ...
MECHANICAL MOUSE OR BALL MOUSE:
This is an article that I came
across from my recent readings. Hope you'll find it useful.
We are are surrounded with technology. We have computers, we have a really interesting device with which we control almost everything. Any guesses? Exactly, the mouse.
And there are different types of mouse. But have you used all of them, wireless, gstick, optical, trackball, mechanical? Let’s talk about all of them and how they work.
WIRELESS MOUSE:
The Mouse without wire or cord is called wireless mouse or cordless mouse. Most wireless mice use radiofrequency (RF) technology to communicate information to your computer. Since RF devices require two main components: a transmitter and a receiver,thats why wireless mouse also requires it.
Working :
• The transmitter is housed in the mouse. It sends an electromagnetic (radio) signal that encodes the information about the mouse’s movements and the buttons you click.
• The receiver, which is connected to your computer, accepts the signal, decodes it and passes it on to the mouse driver software and your computer’s operating system.
• The receiver can be a separate device that plugs into your computer, a special card that you place in an expansion slot, or a built-in component.
GSTICK MOUSE:
Gordon Stewart designed the Stick to add a more authentic and natural feel to artistic manipulations on both Macs and PCs. These mice are Wireless and pocket-sized. It looks like a pencil. gStick mouse is like a pencil. It can be used for web browsing, office work or whatever you do with your traditional mouse, with more comfort. It also features a scroll wheel that can be manipulated with a finger or thumb a button on either side of the wheel. It’s claimed that a single AAA battery will power the gStick for between three and five months.
OPTICAL MOUSE:
An optical mouse is an computer pointing device that uses a light-emitting diode an optical sensor, and digital signal processing ( DSP ).This mouse doesn’t have mouse ball and electromechanical transducer. Movement is detected by sensing changes in reflected light, instead of interpreting the motion of a rolling sphere.
an optical mouse does not have moving parts thats why there is no need of cleaning .Also there is no mechanical fatigue and failure in this type of mice. The optical mouse takes microscopic snapshots of the working surface at a rate of more than 1,000 images per second. If the mouse is moved, the image changes . The best surfaces reflect but scatter light; an example is a blank sheet of white drawing paper. Some surfaces do not allow the sensor and DSP to function properly because the irregularities are too small to be detected. An example of a poor optical-mousing surface is unfrosted glass.
A TRACKBALL MOUSE:
A trackball mouse is a pointing device.It consists of a ball held by a socket containing sensors to detect a rotation of the ball. The user rolls the ball with the thumb, fingers, or the palm of the hand to move a pointer. the operator just continues rolling with trackball but a mouse would have to be lifted and re-positioned. Some trackballs, such as Logitech’s optical-pickoff types, have notably low friction, as well as being dense (glass), so they can be spun to make them coast. Large trackballs are common on CAD workstations.
MECHANICAL MOUSE OR BALL MOUSE:
In 1972, Bill English (builder of Engelbart’s original mouse) invented the ball mouse, while working for Xerox PARC. In this, a single mouse was replaced by the external wheels, which could roll in any direction.
Mechanical mouse is a device integrated with an internal metal or rubber ball, which can spin in all directions (left, right, up and down). Thus, the display cursor moves as the mouse detects the direction. The ball in the mechanical mouse spins when it comes in contact with surface on which it is placed
COMPUTER KEYBOARD
In computing, a computer keyboard is a typewriter-style device which uses an arrangement of buttons or keys to act as a mechanical lever or electronic switch. Following the decline of punch cards and paper tape, interaction via teleprinter-style keyboards became the main input device for computers.
A keyboard typically has characters engraved or printed on the keys (buttons) and each press of a key typically corresponds to a single written symbol. However, to produce some symbols requires pressing and holding several keys simultaneously or in sequence. While most keyboard keys produce letters, numbers or signs (characters), other keys or simultaneous key presses can produce actions or execute computer commands.
Despite the development of alternative input devices, such as the mouse, touchscreen, pen devices, character recognition and voice recognition, the keyboard remains the most commonly used device for direct (human) input of alphanumeric data into computers.
In normal usage, the keyboard is used as a text entry interface to type text and numbers into a word processor, text editor or other programs. In a modern computer, the interpretation of key presses is generally left to the software. A computer keyboard distinguishes each physical key from every other and reports all key presses to the controlling software. Keyboards are also used for computer gaming, either with regular keyboards or by using keyboards with special gaming features, which can expedite frequently used keystroke combinations. A keyboard is also used to give commands to the operating system of a computer, such as Windows' Control-Alt-Delete combination, which brings up a task window or shuts down the machine. A command-line interface is a type of user interface operated entirely through a keyboard, or another device doing the job of one.
Keyboard types
One factor determining the size of a keyboard is the presence of duplicate keys, such as a separate numeric keyboard, for convenience.
Further the keyboard size depends on the extent to which a system is used where a single action is produced by a combination of subsequent or simultaneous keystrokes (with modifier keys, see below), or multiple pressing of a single key. A keyboard with few keys is called a keypad. See also text entry interface.
Another factor determining the size of a keyboard is the size and spacing of the keys. Reduction is limited by the practical consideration that the keys must be large enough to be easily pressed by fingers. Alternatively a tool is used for pressing small keys.
STANDARD KEYBOARD
Standard alphanumeric keyboards have keys that are on three-quarter inch centers (0.750 inches, 19.05 mm)[citation needed], and have a key travel of at least 0.150 inches (3.81 mm). Desktop computer keyboards, such as the 101-key US traditional keyboards or the 104-key Windows keyboards, include alphabetic characters, punctuation symbols, numbers and a variety of function keys. The internationally common 102/104 key keyboards have a smaller left shift key and an additional key with some more symbols between that and the letter to its right (usually Z or Y). Also the enter key is usually shaped differently. Computer keyboards are similar to electric-typewriter keyboards but contain additional keys, such as the command or Windows keys. There is no standard computer keyboard, although many manufacture imitate the keyboard of PCs. There are actually three different PC keyboard: the original PC keyboard with 84 keys, the AT keyboard also with 84 keys and the enhanced keyboard with 101 keys. The three differ somewhat in the placement of function keys, the control keys, the return key, and the shift key.
Laptop-size
Laptop keyboard with its keys (except the space bar) removed, revealing crumbs, pet hair and other detritus to be cleaned away.
Keyboards on laptops and notebook computers usually have a shorter travel distance for the keystroke, shorter over travel distance, and a reduced set of keys. They may not have a numerical keypad, and the function keys may be placed in locations that differ from their placement on a standard, full-sized keyboard. The switch mechanism for a laptop keyboard is more likely to be a scissor switch than a rubber dome; this is opposite the trend for full-size keyboards.
FLEXIBLE KEYBOARD
Flexible keyboards are a junction between normal type and laptop type keyboards: normal from the full arrangement of keys, and laptop from the short key distance. Additionally, the flexibility allows the user to fold/roll the keyboard for better storage and transfer. However, for typing the keyboard must be resting on a hard surface. The vast majority of flexible keyboards in the market are made from silicone; this material makes them water and dust proof, a very pleasant feature especially in hospitals where keyboards are subjected to frequent washing. For connection with the computer the keyboards use a USB cable, and operating system support reaches as far back as Windows 2000.
Handheld
An AlphaGrip handheld keyboard
Handheld ergonomic keyboards are designed to be held like a game controller, and can be used as such, instead of laid out flat on top of a table surface. Typically handheld keyboards hold all the alphanumeric keys and symbols that a standard keyboard would have, yet only be accessed by pressing two sets of keys at once; one acting as a function key similar to a 'Shift' key that would allow for capital letters on a standard keyboard.[2] Handheld keyboards allow the user the ability to move around a room or to lean back on a chair while also being able to type in front or away from the computer.[3] Some variations of handheld ergonomic keyboards also include a trackball mouse that allow mouse movement and typing included in one handheld device
Handheld
An AlphaGrip handheld keyboard
Handheld ergonomic keyboards are designed to be held like a game controller, and can be used as such, instead of laid out flat on top of a table surface. Typically handheld keyboards hold all the alphanumeric keys and symbols that a standard keyboard would have, yet only be accessed by pressing two sets of keys at once; one acting as a function key similar to a 'Shift' key that would allow for capital letters on a standard keyboard.[2] Handheld keyboards allow the user the ability to move around a room or to lean back on a chair while also being able to type in front or away from the computer.[3] Some variations of handheld ergonomic keyboards also include a trackball mouse that allow mouse movement and typing included in one handheld device.
The keyboards on laptops usually have a shorter travel distance and a reduced set of keys.
Thumb-sized
Smaller external keyboards have been introduced for devices without a built-in keyboard, such as PDAs, and smartphones. Small keyboards are also useful where there is a limited workspace.
A chorded keyboard allows users to press several keys simultaneously. For example, the GKOS keyboard has been designed for small wireless devices. Other two-handed alternatives more akin to a game controller, such as the AlphaGrip, are also used to input data and text.
A thumb keyboard (thumb board) is used in some personal digital assistants such as the Palm Treo and BlackBerry and some Ultra-Mobile PCs such as the OQO.
Numeric keyboards contain only numbers, mathematical symbols for addition, subtraction, multiplication, and division, a decimal point, and several function keys. They are often used to facilitate data entry with smaller keyboards that do not have a numeric keypad, commonly those of laptop computers. These keys are collectively known as a numeric pad, numeric keys, or a numeric keypad, and it can consist of the following types of keys: Arithmetic operators, numbers, arrow keys, Navigation keys, Num Lock and Enter key.
Multifunctional
Multifunction keyboard with LCD function keys.
Multifunctional keyboards provide additional function beyond the standard keyboard. Many are programmable, configurable computer keyboards and some control multiple PCs, workstations (incl. SUN) and other information sources (incl. Thomson Reuters FXT/Eikon, Bloomberg, EBS, etc.) usually in multi-screen work environments. Users have additional key functions as well as the standard functions and can typically use a single keyboard and mouse to access multiple sources.
Multifunction keyboard with custom keys and touchscreen.
Multifunctional keyboards may feature customised keypads, fully programmable function or soft keys for macros/pre-sets, biometric or smart card readers, trackballs, etc. New generation multifunctional keyboards feature a touchscreen display to stream video, control audio visual media and alarms, execute application inputs, configure individual desktop environments, etc. Multifunctional keyboards may also permit users to share access to PCs and other information sources. Multiple interfaces (serial, USB, audio, Ethernet, etc.) are used to integrate external devices. Some multifunctional keyboards are also used to directly and intuitively control video walls.
Common environments for multifunctional keyboards are complex, high-performance workplaces for financial traders and control room operators (emergency services, security, air traffic management; industry, utilities management, etc.).
Non-standard layout and special-use types
Chorded
Main article: Chorded keyboard
While other keyboards generally associate one action with each key, chorded keyboards associate actions with combinations of key presses. Since there are many combinations available, chorded keyboards can effectively produce more actions on a board with fewer keys. Court reporters' stenotype machines use chorded keyboards to enable them to enter text much faster by typing a syllable with each stroke instead of one letter at a time. The fastest typists (as of 2007) use a stenograph, a kind of chorded keyboard used by most court reporters and closed-caption reporters. Some chorded keyboards are also made for use in situations where fewer keys are preferable, such as on devices that can be used with only one hand, and on small mobile devices that don't have room for larger keyboards. Chorded keyboards are less desirable in many cases because it usually takes practice and memorization of the combinations to become proficient.
Software
Software keyboards or on-screen keyboards often take the form of computer programs that display an image of a keyboard on the screen. Another input device such as a mouse or a touchscreen can be used to operate each virtual key to enter text. Software keyboards have become very popular in touchscreen enabled cell phones, due to the additional cost and space requirements of other types of hardware keyboards. Microsoft Windows, Mac OS X, and some varieties of Linux include on-screen keyboards that can be controlled with the mouse. In software keyboards, the mouse has to be maneuvered onto the on-screen letters given by the software. On the click of a letter, the software writes the respective letter on the respective spot.
Projection (as by laser)
Projection keyboards project an image of keys, usually with a laser, onto a flat surface. The device then uses a camera or infrared sensor to "watch" where the user's fingers move, and will count a key as being pressed when it "sees" the user's finger touch the projected image. Projection keyboards can simulate a full size keyboard from a very small projector. Because the "keys" are simply projected images, they cannot be felt when pressed. Users of projected keyboards often experience increased discomfort in their fingertips because of the lack of "give" when typing. A flat, non-reflective surface is also required for the keys to be projected. Most projection keyboards are made for use with PDAs and smartphones due to their small form factor.
Optical keyboard technology
Further information: Keyboard technology
Also known as photo-optical keyboard, light responsive keyboard, photo-electric keyboard and optical key actuation detection technology.
An optical keyboard technology utilizes light emitting devices and photo sensors to optically detect actuated keys. Most commonly the emitters and sensors are located in the perimeter, mounted on a small PCB. The light is directed from side to side of the keyboard interior and it can only be blocked by the actuated keys. Most optical keyboards require at least 2 beams (most commonly vertical beam and horizontal beam) to determine the actuated key. Some optical keyboards use a special key structure that blocks the light in a certain pattern, allowing only one beam per row of keys (most commonly horizontal beam).
Layout
Alphabetic
Main article: Keyboard layout
The 104-key PC US English QWERTY keyboard layout evolved from the standard typewriter keyboard, with extra keys for computing.
The Dvorak Simplified Keyboard layout arranges keys so that frequently used keys are easiest to press, which reduces muscle fatigue when typing common English.
There are a number of different arrangements of alphabetic, numeric, and punctuation symbols on keys. These different keyboard layouts arise mainly because different people need easy access to different symbols, either because they are inputting text in different languages, or because they need a specialized layout for mathematics, accounting, computer programming, or other purposes. The United States keyboard layout is used as default in the currently most popular operating systems: Windows,[4] Mac OS X[5] and Linux.[6][7] The common QWERTY-based layout was designed early in the era of mechanical typewriters, so its ergonomics were compromised to allow for the mechanical limitations of the typewriter.
As the letter-keys were attached to levers that needed to move freely, inventor Christopher Sholes developed the QWERTY layout to reduce the likelihood of jamming. With the advent of computers, lever jams are no longer an issue, but nevertheless, QWERTY layouts were adopted for electronic keyboards because they were widely used. Alternative layouts such as the Dvorak Simplified Keyboard are not in widespread use.
The QWERTZ layout is widely used in Germany and much of Central Europe. The main difference between it and QWERTY is that Y and Z are swapped, and most special characters such as brackets are replaced by diacritical characters.
Another situation takes place with "national" layouts. Keyboards designed for typing in Spanish have some characters shifted, to release the space for Ñ ñ; similarly, those for Portuguese, French and other European languages may have a special key for the character Ç ç. The AZERTY layout is used in France, Belgium and some neighbouring countries. It differs from the QWERTY layout in that the A and Q are swapped, the Z and W are swapped, and the M is moved from the right of N to the right of L (where colon/semicolon is on a US keyboard). The digits 0 to 9 are on the same keys, but to be typed the shift key must be pressed. The unshifted positions are used for accented characters.
Keyboards in many parts of Asia may have special keys to switch between the Latin character set and a completely different typing system. Japanese layout keyboards can be switched between various Japanese input methods and the Latin alphabet by signaling the operating system's input interpreter of the change, and some operating systems (namely the Windows family) interpret the character "\" as "¥" for display purposes without changing the bytecode which has led some keyboard makers to mark "\" as "¥" or both. In the Arab world, keyboards can often be switched between Arabic and Latin characters.
In bilingual regions of Canada and in the French-speaking province of Québec, keyboards can often be switched between an English and a French-language keyboard; while both keyboards share the same QWERTY alphabetic layout, the French-language keyboard enables the user to type accented vowels such as "é" or "à" with a single keystroke. Using keyboards for other languages leads to a conflict: the image on the key does not correspond to the character. In such cases, each new language may require an additional label on the keys, because the standard keyboard layouts do not share even similar characters of different languages (see the example in the figure above).
Key types
Alphanumeric
A Hebrew keyboard lets the user type in both Hebrew and the Latin alphabet.
A Greek keyboard lets the user type in both Greek and the Latin alphabet (MacBook Pro).
The Control, Windows, and Alt keys are important modifier keys.
A Space-cadet keyboard has many modifier keys.
Alphabetical, numeric, and punctuation keys are used in the same fashion as a typewriter keyboard to enter their respective symbol into a word processing program, text editor, data spreadsheet, or other program. Many of these keys will produce different symbols when modifier keys or shift keys are pressed. The alphabetic characters become uppercase when the shift key or Caps Lock key is depressed. The numeric characters become symbols or punctuation marks when the shift key is depressed. The alphabetical, numeric, and punctuation keys can also have other functions when they are pressed at the same time as some modifier keys. The Space bar is a horizontal bar in the lowermost row, which is significantly wider than other keys. Like the alphanumeric characters, it is also descended from the mechanical typewriter. Its main purpose is to enter the space between words during typing. It is large enough so that a thumb from either hand can use it easily. Depending on the operating system, when the space bar is used with a modifier key such as the control key, it may have functions such as resizing or closing the current window, half-spacing, or backspacing. In computer games and other applications the key has myriad uses in addition to its normal purpose in typing, such as jumping and adding marks to check boxes. In certain programs for playback of digital video, the space bar is used for pausing and resuming the playback.
Modifier keys
Modifier keys are special keys that modify the normal action of another key, when the two are pressed in combination. For example, + in Microsoft Windows will close the program in an active window. In contrast, pressing just will probably do nothing, unless assigned a specific function in a particular program. By themselves, modifier keys usually do nothing. The most widely used modifier keys include the Control key, Shift key and the Alt key. The AltGr key is used to access additional symbols for keys that have three symbols printed on them. On the Macintosh and Apple keyboards, the modifier keys are the Option key and Command key, respectively. On MIT computer keyboards, the Meta key is used as a modifier and for Windows keyboards, there is a Windows key. Compact keyboard layouts often use a Fn key. "Dead keys" allow placement of a diacritic mark, such as an accent, on the following letter (e.g., the Compose key). The Enter/Return key typically causes a command line, window form or dialog box to operate its default function, which is typically to finish an "entry" and begin the desired process. In word processing applications, pressing the enter key ends a paragraph and starts a new one.
Cursor keys
Navigation keys or cursor keys include a variety of keys which move the cursor to different positions on the screen. Arrow keys are programmed to move the cursor in a specified direction; page scroll keys, such as the Page Up and Page Down keys, scroll the page up and down. The Home key is used to return the cursor to the beginning of the line where the cursor is located; the End key puts the cursor at the end of the line. The Tab key advances the cursor to the next tab stop. The Insert key is mainly used to switch between overtype mode, in which the cursor overwrites any text that is present on and after its current location, and insert mode, where the cursor inserts a character at its current position, forcing all characters past it one position further. The Delete key discards the character ahead of the cursor's position, moving all following characters one position "back" towards the freed place. On many notebook computer keyboards the key labeled Delete (sometimes Delete and Backspace are printed on the same key) serves the same purpose as a Backspace key. The Backspace key deletes the preceding character. Lock keys lock part of a keyboard, depending on the settings selected. The lock keys are scattered around the keyboard. Most styles of keyboards have three LEDs indicating which locks are enabled, in the upper right corner above the numeric pad. The lock keys include Scroll lock, Num lock (which allows the use of the numeric keypad), and Caps lock.
System commands
The SysRq and Print screen commands often share the same key. SysRq was used in earlier computers as a "panic" button to recover from crashes (and it is still used in this sense to some extent by the Linux kernel; see Magic SysRq key). The Print screen command used to capture the entire screen and send it to the printer, but in the present it usually puts a screenshot in the clipboard. The Break key/Pause key no longer has a well-defined purpose. Its origins go back to teleprinter users, who wanted a key that would temporarily interrupt the communications line. The Break key can be used by software in several different ways, such as to switch between multiple login sessions, to terminate a program, or to interrupt a modem connection. In programming, especially old DOS-style BASIC, Pascal and C, Break is used (in conjunction with Ctrl) to stop program execution. In addition to this, Linux and variants, as well as many DOS programs, treat this combination the same as Ctrl+C. On modern keyboards, the break key is usually labeled Pause/Break. In most Windows environments, the key combination Windows key+Pause brings up the system properties. The Escape key (often abbreviated Esc) is used to initiate an escape sequence. As most computer users no longer are concerned with the details of controlling their computer's peripherals, the task for which the escape sequences were originally designed, the escape key was appropriated by application programmers, most often to "escape" or back out of a mistaken command. This use continues today in Microsoft Windows's use of escape as a shortcut in dialog boxes for No, Quit, Exit, Cancel, or Abort. A common application today of the Esc key is as a shortcut key for the Stop button in many web browsers. On machines running Microsoft Windows, prior to the implementation of the Windows key on keyboards, the typical practice for invoking the "start" button was to hold down the control key and press escape. This process still works in Windows 2000, XP, Vista, 7, 8, and 10. The Enter key is located: One in the alphanumeric keys and the other one is in the numeric keys. When one worked something on their computer and wanted to do something with their work, pressing the enter key would do the command they ordered. Another function is to create a space for next paragraph. When one typed and finished typing a paragraph and they wanted to have a second paragraph, they could press enter and it would do spacing. Shift key: when one presses shift and a letter, it will capitalize the letter pressed with the shift key. Another use is to type more symbols than appear to be available, for instance the apostrophe key is accompanied with a quotation mark on the top. If one wants to type the quotation mark but pressed that key alone, the symbol that would appear would be the apostrophe. The quotation mark will only appear if both the required key and the Shift key are pressed. The Menu key or Application key is a key found on Windows-oriented computer keyboards. It is used to launch a context menu with the keyboard rather than with the usual right mouse button. The key's symbol is usually a small icon depicting a cursor hovering above a menu. On some Samsung keyboards the cursor in the icon is not present, showing the menu only. This key was created at the same time as the Windows key. This key is normally used when the right mouse button is not present on the mouse. Some Windows public terminals do not have a Menu key on their keyboard to prevent users from right-clicking (however, in many Windows applications, a similar functionality can be invoked with the Shift+F10 keyboard shortcut).
Miscellaneous
Multimedia buttons on some keyboards give quick access to the Internet or control the volume of the speakers.
Many, but not all,computer keyboards have a numeric keypad to the right of the alphabetic keyboard which contains numbers, basic mathematical symbols (e.g., addition, subtraction, etc.), and a few function keys. On Japanese/Korean keyboards, there may be Language input keys for changing the language to use. Some keyboards have power management keys (e.g., power key, sleep key and wake key); Internet keys to access a web browser or E-mail; and/or multimedia keys, such as volume controls or keys that can be programmed by the user to launch a specified software or command like launching a game or minimize all windows.
Numeric keys
When we calculate, we use these numeric keys to type numbers. Symbols concerned with calculations such as addition, subtraction, multiplication and division symbols are located in this group of keys. The enter key in this keys indicate the equal sign.
Multiple layouts
It is possible to install multiple keyboard layouts within an operating system and switch between them, either through features implemented within the OS, or through an external application. Microsoft Windows,[8] Linux,[9] and Mac[10] provide support to add keyboard layouts and choose from them.
Layout changing software
The character code produced by any key press is determined by the keyboard driver software. A key press generates a scancode which is interpreted as an alphanumeric character or control function. Depending on operating systems, various application programs are available to create, add and switch among keyboard layouts. Many programs are available, some of which are language specific.
The arrangement of symbols of specific language can be customized. An existing keyboard layout can be edited, and a new layout can be created using this type of software.
For example, Ukelele [sic] for Mac,[11] The Microsoft Keyboard Layout Creator[12] and open-source Avro Keyboard for Windows provide the ability to customize the keyboard layout as desired.
Illumination
Keyboards and keypads may be illuminated from inside, especially on equipment for mobile use. Illumination facilitates the use of the keyboard or keypad in dark environments. Some gaming keyboards have lighted keys, to make it easier for gamers to find command keys while playing in a dark room. Some keyboards may have small LED lights in a few important function keys, to remind users that the function is activated